In the wild world of cybersecurity, threats are like bears—big, unpredictable, and potentially dangerous. Understanding how to assess these risks is crucial for anyone involved in protecting digital assets. “Bear security risk assessment methods” serves as an essential guide, helping you navigate through the dense forest of potential threats with confidence and precision.
Read Now : United Bear’s Competitive Market Approach
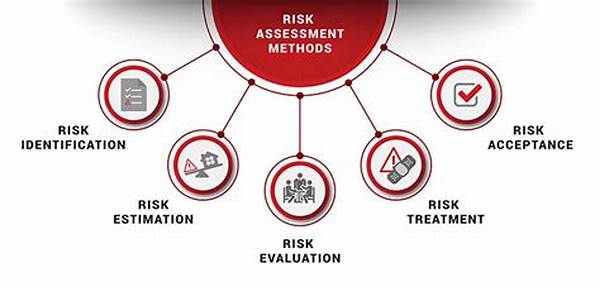
Breaking It Down: Bear Security Risk Assessment Methods
Alright, let’s get down to business. “Bear security risk assessment methods” can sound like a mouthful, but it’s all about sizing up those digital threats lurking in the shadows. Imagine you’re on a trail, and you spot a bear. First, you gotta size up its mood, right? Same thing here—evaluate how mean or mellow those digital bears are. Next, gotta figure out their hangout spots, aka vulnerable points in your system. Lastly, have a game plan: know when to stand your ground with robust defenses or when to retreat with tight security protocols. It’s all about being prepared for whatever surprise those tricky cyber bears throw your way. So, prep up, and face those threats like a pro!
The Lowdown: Core Strategies in Bear Security Risk Assessment Methods
1. Spotting the Bears: Identify potential threats lurking in your network. Bear security risk assessment methods help you sniff out cyber threats like a bloodhound on a scent trail.
2. Weighing the Risk: Gauge how serious these threats are. Some are just curious grizzlies, while others are angry mama bears.
3. Vulnerability Check-Up: Take a look at where your defenses are weakest. Just like checking a campsite for bear tracks, know where you’re most vulnerable.
4. Action Plan: Plan your defense like a seasoned bear handler. Know when to play dead, when to run, and when to stand your ground.
5. Regular Drills: Keep those claws sharp—practice makes perfect. Use bear security risk assessment methods regularly to keep your defenses top-notch.
Read Now : “assessment Methods For Bear Sustainability”
The Essence of Bear Security Risk Assessment Methods
When venturing into the realm of cybersecurity, bear security risk assessment methods are like a trusty guide navigating you through a digital forest. Imagine each cyber threat as a grumpy bear; you need to assess how likely they are to bite. These methods equip you with the know-how to measure the likelihood and impact of potential threats. From identifying where the bears are to figuring out how best to handle them, you’re all set. With technology advancing at a breakneck speed, new threats, like new bears, are always on the horizon. But don’t sweat it—just arm yourself with the right toolkit, and you’ll be dodging those digital claws with ease.
Key Takeaways on Bear Security Risk Assessment Methods
Bear security risk assessment methods are a powerhouse, packing a punch in the cybersecurity sphere. Here’s the scoop: the key is to know your enemy. Understand the different types of bears—some threats are tiny like cubs, while others are massive grizzlies. Next up, have the 411 on their behavior. Some threats move fast and chaotic, while others stealthily lurk about. Always have your cybersecurity campfire burning bright, keeping those threats at bay. Seriously, knowledge is your best weapon, and with bear security risk assessment methods, you’ve got the ultimate guide to keep your digital den safe and sound!
Wrapping It All Up: Bear Security Risk Assessment Methods Decoded
Unlocking the secrets of bear security risk assessment methods is like deciphering the code to a digital adventure. Know this: identifying threats is step one. Just like knowing if a bear’s just passing by or getting ready to raid your picnic. The trick? Stay one step ahead. Regular checkups ensure your defenses are always a notch above the prowling threats. In this crazy, ever-evolving digital landscape, you don’t just need to survive; you gotta thrive. With bear security risk assessment methods in your toolkit, you’ll be tackling those digital bears head-on like a true cyberspace ranger.
Final Thoughts: The Backstory on Bear Security Risk Assessment Methods
In our tech-driven jungle, keeping your digital campsite secure is crucial. Bear security risk assessment methods are all about staying alert and ready for any potential cyber threat. Know the risks, plan your defenses, and keep your systems updated—because in the digital world, just like in the wild, it’s all about survival of the smartest. Keep those eyes sharp and gear up against those sneaky cyber bears lurking around; with these methods under your belt, you’re ready for anything coming your way!